Cybercriminals are always looking for ways to steal your personal data. We've seen a huge uptick in the number of data breaches over the past few years.
It's not always your information that the criminal is after though. Sometimes the thief is just looking to steal your gadget, for either personal use or to sell for profit.
That's why you need to know these three ways hackers can bypass your Android passcode, and how you can stop them.
International Mobile Equipment Identification (IMEI)
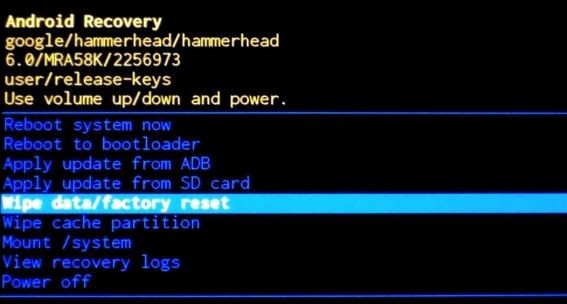
If a thief steals your Android gadget for use or sale, they are not necessarily going to be concerned with saving your favorite apps. An easy way for them to bypass your passcode is to perform a factory reset. By doing this, everything on your phone will be deleted.During the factory reset process, the criminal will select the wipe data/factory reset option.
How to block your stolen gadget from being used
All mobile phones have an International Mobile Equipment Identification (IMEI). This is a unique identification number found on every device.When you turn on your phone, the SIM card registers your IMEI number to the service providers' server and is permanently stored in its database. If your phone is stolen, you can use this IMEI number to have the phone's service cut off.
Here are the steps you need to take to cut off your stolen phone's service:
- Find your IMEI number - Obviously, this step needs to be completed before your phone is stolen. The easiest way to find the IMEI number is to open the phone's dialer as if you were making a call >> type Star Pound Zero Six Pound >> this will display the phone's IMEI number. This option isn't available on all carriers. For those who don't have this option, you can find the IMEI number under Settings >> About Phone >> Status >> IMEI information >> the IMEI number is displayed here. Once you have this number, write it down and store it in a safe place.
- Report stolen phone to the police - Call the police and tell them your phone has been stolen. Make sure to give them the IMEI number and have them put it in the report.
- Call your service provider - After filing the police report, call your service provider and ask them to block the IMEI number. They require the police report number before they will do this to avoid pranksters shutting off someone's phone without it actually being stolen. All of the major mobile providers use the same IMEI blocked number list, so if you only report it stolen with your provider it will still be blocked on the other mobile networks.
Android Debug Bridge (ADB)
If your phone has USB debugging turned on, hackers can delete the password file using a desktop tool called Android Debug Bridge (ADB). A hacker can connect your Android phone to a computer via USB and simply run a command via a command prompt window from an ADB directory.To prevent this hack, make sure you disable USB debugging on your Android phone by going to Settings >> Developer Options (If enabled) >> scroll down to Debugging then toggle USB debugging to off.
Alternatively, you can turn off Developer options altogether.
Important: If you don’t have the Developer options on your Settings app, don’t worry, it’s not turned on by default. It is a secret section recommended strictly for advanced users. The secret way to turn it on is by going to Settings >> About Phone then scroll down to the Build Number and tap it seven times.
Booting into safe mode
If you’re using a third-party app to lock your screen, hackers can simply boot into safe mode to bypass that lock screen.To prevent this from happening to you, don’t rely on third-party lock screen apps. Not only are they security risks themselves, they can be bypassed easily.